cyber monday 2024 Cyberbullying gifs
If you are searching about Cyber Crime Concept | Cyber, Crime, Technology posters you’ve visit to the right page. We have 35 Pictures about Cyber Crime Concept | Cyber, Crime, Technology posters like File Encryption online and free, Cybersecurity Framework 101 — A Comprehensive Guide To Cybersecurity and also Cyber Digital por Hmtek2323 - Amazfit T-Rex | 🇺🇦 Catálogo de Watch. Here you go:
Cyber Crime Concept | Cyber, Crime, Technology Posters
 www.pinterest.comCyber Crime Concept | Cyber, Crime, Technology posters
www.pinterest.comCyber Crime Concept | Cyber, Crime, Technology posters
Departamento Arauco
 aimogasta.tripod.comDepartamento Arauco
aimogasta.tripod.comDepartamento Arauco
Cyber Security PNG Images Transparent Free Download
 www.pngmart.comCyber Security PNG Images Transparent Free Download
www.pngmart.comCyber Security PNG Images Transparent Free Download
Abstract Future Technology Concept Cyber Hitech Stock Vector (Royalty
 www.shutterstock.comAbstract Future Technology Concept Cyber Hitech Stock Vector (Royalty …
www.shutterstock.comAbstract Future Technology Concept Cyber Hitech Stock Vector (Royalty …
Pin On Beau
 www.pinterest.dePin on Beau
www.pinterest.dePin on Beau
Cyber Security Vector Illustration 486202 Vector Art At Vecteezy
 www.vecteezy.comCyber Security Vector Illustration 486202 Vector Art at Vecteezy
www.vecteezy.comCyber Security Vector Illustration 486202 Vector Art at Vecteezy
Cybersecurity Framework 101 — A Comprehensive Guide To Cybersecurity
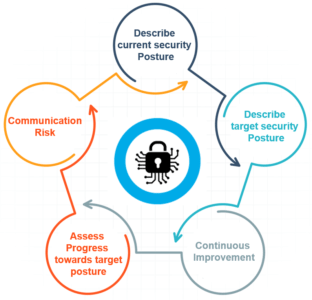 medium.comCybersecurity Framework 101 — A Comprehensive Guide To Cybersecurity …
medium.comCybersecurity Framework 101 — A Comprehensive Guide To Cybersecurity …
Seguridad Vectores, Iconos, Gráficos Y Fondos Para Descargar Gratis
 es.vecteezy.comSeguridad Vectores, Iconos, Gráficos y Fondos para Descargar Gratis
es.vecteezy.comSeguridad Vectores, Iconos, Gráficos y Fondos para Descargar Gratis
Constituents Of Cyber-physical Attack | Download Scientific Diagram
 www.researchgate.netConstituents of cyber-physical attack | Download Scientific Diagram
www.researchgate.netConstituents of cyber-physical attack | Download Scientific Diagram
Help Build My Perfect PC | Cyberpower Uk
 www.cyberpowersystem.co.ukHelp Build My Perfect PC | Cyberpower uk
www.cyberpowersystem.co.ukHelp Build My Perfect PC | Cyberpower uk
Cyberbullying GIFs | Tenor
 tenor.comCyberbullying GIFs | Tenor
tenor.comCyberbullying GIFs | Tenor
Mammoth Cyber Enterprise Software And Services Reviews
 www.gartner.comMammoth Cyber Enterprise Software and Services Reviews
www.gartner.comMammoth Cyber Enterprise Software and Services Reviews
Top-10 Cyber Threats Pie Chart. | Download Scientific Diagram
 www.researchgate.netTop-10 cyber threats pie chart. | Download Scientific Diagram
www.researchgate.netTop-10 cyber threats pie chart. | Download Scientific Diagram
Cyber Security
 decodedcyber.comCyber Security
File Encryption Online And Free
 www.kfcipher.netFile Encryption online and free
www.kfcipher.netFile Encryption online and free
데스크 벽지 사이버 배경 해커 | 프리미엄 사진
 kr.freepik.com데스크 벽지 사이버 배경 해커 | 프리미엄 사진
kr.freepik.com데스크 벽지 사이버 배경 해커 | 프리미엄 사진
Randomlabs:Welcome ON_BOARD ! Welcome On Board, Sentient, Riddles
 www.pinterest.comrandomlabs:Welcome ON_BOARD ! Welcome On Board, Sentient, Riddles …
www.pinterest.comrandomlabs:Welcome ON_BOARD ! Welcome On Board, Sentient, Riddles …
Cyber Attack Logo
 utpaqp.edu.peCyber Attack Logo
utpaqp.edu.peCyber Attack Logo
Top 10 Operational Responses To The GDPR – Part 1: Data Inventory And
 iapp.orgTop 10 operational responses to the GDPR – Part 1: Data inventory and …
iapp.orgTop 10 operational responses to the GDPR – Part 1: Data inventory and …
Learn About Cyber Security
 codingireland.ieLearn about Cyber Security
codingireland.ieLearn about Cyber Security
Pro Cybercrime Law
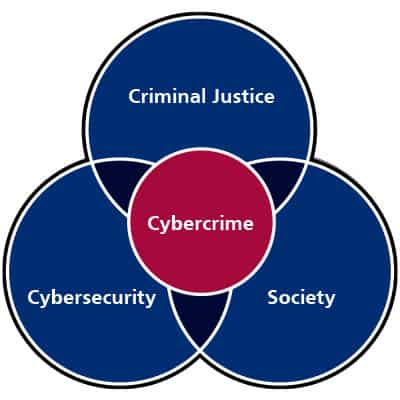 ar.inspiredpencil.comPro Cybercrime Law
ar.inspiredpencil.comPro Cybercrime Law
Mapping The NIST Cybersecurity Framework To SearchLight: Eating Our Own
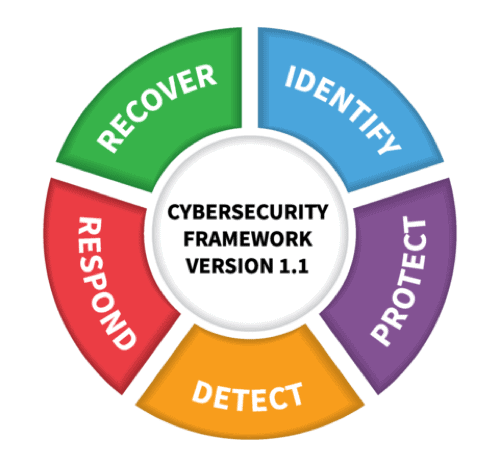 www.digitalshadows.comMapping the NIST Cybersecurity Framework to SearchLight: Eating our own …
www.digitalshadows.comMapping the NIST Cybersecurity Framework to SearchLight: Eating our own …
Core Principles Of Cybersecurity
 tutorials.ducatindia.comCore Principles of Cybersecurity
tutorials.ducatindia.comCore Principles of Cybersecurity
Corporate Hacking: Are You A Target? - IEEE Innovation At Work
 innovationatwork.ieee.orgCorporate Hacking: Are You a Target? - IEEE Innovation at Work
innovationatwork.ieee.orgCorporate Hacking: Are You a Target? - IEEE Innovation at Work
Cyber Security Awareness, Safe Internet, Relationship Blogs, Cute
 www.pinterest.atCyber Security Awareness, Safe Internet, Relationship Blogs, Cute …
www.pinterest.atCyber Security Awareness, Safe Internet, Relationship Blogs, Cute …
Cyber-Naturarzt - Naturarztpraxis - Traditionelle Heilkunde - Cyber
 cyber-natdoc.comCyber-Naturarzt - Naturarztpraxis - Traditionelle Heilkunde - Cyber …
cyber-natdoc.comCyber-Naturarzt - Naturarztpraxis - Traditionelle Heilkunde - Cyber …
Cyber Resilience Lifecycle. | Download Scientific Diagram
 www.researchgate.netCyber Resilience Lifecycle. | Download Scientific Diagram
www.researchgate.netCyber Resilience Lifecycle. | Download Scientific Diagram
Computer Security Computer Icons Information Security Information
 www.pngegg.comComputer security Computer Icons Information security Information …
www.pngegg.comComputer security Computer Icons Information security Information …
One Step Beyond Cyber
 onestepbeyondcyberpodcast.buzzsprout.comOne Step Beyond Cyber
Cyber Sci-Fi GIF By BADCODEC - Find & Share On GIPHY
 giphy.comCyber Sci-Fi GIF by BADCODEC - Find & Share on GIPHY
giphy.comCyber Sci-Fi GIF by BADCODEC - Find & Share on GIPHY
The Reason Why Windows 11 Might Not Come To Most PCs(and Why Microsoft
 www.tzperspective.comThe Reason why Windows 11 might not come to most PCs(and why Microsoft …
www.tzperspective.comThe Reason why Windows 11 might not come to most PCs(and why Microsoft …
Pin On Quick Saves
 in.pinterest.comPin on Quick Saves
in.pinterest.comPin on Quick Saves
Cyber Digital Por Hmtek2323 - Amazfit T-Rex | 🇺🇦 Catálogo De Watch
 amazfitwatchfaces.comCyber Digital por Hmtek2323 - Amazfit T-Rex | 🇺🇦 Catálogo de Watch …
amazfitwatchfaces.comCyber Digital por Hmtek2323 - Amazfit T-Rex | 🇺🇦 Catálogo de Watch …
Abstract Cyber Security Background Digital Vector Image
 www.vectorstock.comAbstract cyber security background digital Vector Image
www.vectorstock.comAbstract cyber security background digital Vector Image
Free Vector | Cyber Monday On Flat Design
 www.freepik.comFree Vector | Cyber monday on flat design
www.freepik.comFree Vector | Cyber monday on flat design
Top 10 operational responses to the gdpr – part 1: data inventory and …. Cyberbullying gifs. Cyber resilience lifecycle.